This week, Prof. Bodden was interviewed by WDR radio regarding an idea put forward by the social-democrat party (SPD) to hold companies liable if they sell insecure software. You can listen to the full interview here (in German).
Category Archives: General
Join our research group as a Doctoral Student or PostDoc!
Featured
We are currently looking for doctoral and postdoctoral researchers to complement our research group at Paderborn university. For further information, please consult our previous announcement here. As stated, please direct your applications to se-jobs.cs@upb.de
For the doctoral level, we encourage you to apply if you have completed your Master degree in either computer science, mathematics, engineering or any related field of study.
At the post-doctoral level, we are particularly looking for candidates with a proven track record (at least two papers at very reputable venues) in any of those subject areas:
- Static and/or dynamic program analysis
- Software Security
- Systems Security
- Applied (!) cryptography and/or cryptanalysis
Steven Arzt and Siegfried Rasthofer win Dissertation Award of the Ernst Denert Foundation
Once a year, the Ernst Denert Foundation (by Ernst Denert, one of the founders of sd&m, now Capgemini), sponsor’s the Software Engineering award, which is given out at the SE conference by the Gesellschaft für Informatik. Usually, this award is given out to a single individual for her or his dissertation.
Just this year, the choice was apparently particularly hard to make: two theses really stood out so much that the jury was unable to decide among them. In result, I am more than happy to announce that both my former Ph.D. students Steven Arzt and Siegfried Rasthofer have been chosen to receive the award for 2018. Congratulations Steven and Siegfried! Well done!
You can access their theses here:
| Improving Mobile-Malware Investigations with Static and Dynamic Code Analysis Techniques , PhD thesis, Technische Universität Darmstadt, 2016. Awarded: Summa cum laude & Fraunhofer IuK Dissertation Award [bib] [pdf] | |
| Static Data Flow Analysis for Android Applications , PhD thesis, Technische Universität Darmstadt, 2016. Awarded: Summa cum laude [bib] [pdf] |
Siegfried Rasthofer wins Fraunhofer IuK Dissertation Award
 At the GI Jahrestagung in Chemnitz, my former Ph.D. Student Siegfried Rasthofer (now research group leader at Fraunhofer SIT) will be awarded the Dissertation Award by the Fraunhofer IuK Verbund, for this thesis Improving Mobile-Malware Investigations with Static and Dynamic Code Analysis Techniques. Congratulations to Siegfried! Well done!
At the GI Jahrestagung in Chemnitz, my former Ph.D. Student Siegfried Rasthofer (now research group leader at Fraunhofer SIT) will be awarded the Dissertation Award by the Fraunhofer IuK Verbund, for this thesis Improving Mobile-Malware Investigations with Static and Dynamic Code Analysis Techniques. Congratulations to Siegfried! Well done!
Looking for Research Group Leader in Software Engineering
At Fraunhofer IEM we are currently looking for a research group leader within our Software Engineering division. German language skills are required. Find more information here
New paper on Just-in-time Code Analysis
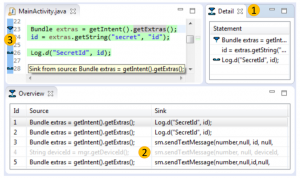 In a collaborative effort with Karim Ali (University of Alberta), Ben Livshits (Imperial College London), Justin Smith and Emerson Murphy-Hill (North Caroline State University), my Ph.D. student Lisa Nguyen and myself have just concluded a new piece of research on Just-in-time (JIT) static code analysis. The approach, which we exemplify with a JIT taint analysis for Android, can be applied to most static analyses
In a collaborative effort with Karim Ali (University of Alberta), Ben Livshits (Imperial College London), Justin Smith and Emerson Murphy-Hill (North Caroline State University), my Ph.D. student Lisa Nguyen and myself have just concluded a new piece of research on Just-in-time (JIT) static code analysis. The approach, which we exemplify with a JIT taint analysis for Android, can be applied to most static analyses 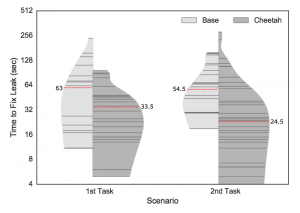 and allows those analyses to execute more efficiently in integrated development environments. In particular, the analysis is tuned such that it executes first in code recently edited by the programmer and then searches its way further “outward” from there. As our experiments indicate, this decreases round-trip times for programmers and hence increases their productivity during the fixing of security vulnerabilities.
and allows those analyses to execute more efficiently in integrated development environments. In particular, the analysis is tuned such that it executes first in code recently edited by the programmer and then searches its way further “outward” from there. As our experiments indicate, this decreases round-trip times for programmers and hence increases their productivity during the fixing of security vulnerabilities.
A preprint of the work, accepted for publication at ISSTA, is now available online, as is our implementation and data set:
Just-in-Time Static Analysis , In International Symposium on Software Testing and Analysis (ISSTA), 2017. (To appear.)
Official inauguration of Fraunhofer IEM
 Today we were very happy to host NRW’s minister of science Svenja Schulze and Fraunhofer’s Director of Science Dr. Raoul Klingner for the official inauguration of Fraunhofer IEM. The new institute is the first to be founded within NRW within the past 20 years, and was bootstrapped in just about seven years – a new record in the Fraunhofer Society.
Today we were very happy to host NRW’s minister of science Svenja Schulze and Fraunhofer’s Director of Science Dr. Raoul Klingner for the official inauguration of Fraunhofer IEM. The new institute is the first to be founded within NRW within the past 20 years, and was bootstrapped in just about seven years – a new record in the Fraunhofer Society.
IEEE S&P Paper on Hardening the Java Runtime is now available
Our new S&P paper Hardening Java’s Access Control by Abolishing Implicit Privilege Elevation is now available online. It is a follow-up work to our previous CCS’16 paper An In-Depth Study of More Than Ten Years of Java Exploitation. In this former paper we classified a large number of history Java exploits. In doing so, we found that the largest class of exploits was made possible by shortcuts in Java’s implementation of access control. In the S&P paper we now show that it is possible to go without those shortcuts, without any loss of performance. We also discuss the usability implications that this removal of shortcuts would have.
New Paper “The Soot-based Toolchain For Analyzing Android Apps”
Steven, Siegfried and I have just completed our invited paper for MOBILESoft’17. The paper The Soot-based Toolchain For Analyzing Android Apps summarizes for the first time the Soot-based tool chain for analyzing Android apps that we have built up over the past years. We hope you will enjoy the read!
And if you attend ICSE, maybe consider attending MOBILESoft as well, and you will be able to attend my keynote talk.
TV Interview on Smart Home Security
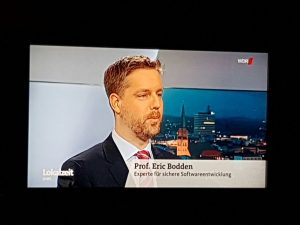 The local television interviewed me today on Smart Home Security. You can watch the video here. Skip to about 9 minutes.
The local television interviewed me today on Smart Home Security. You can watch the video here. Skip to about 9 minutes.
