We are looking for an interested student who wants to write her/his bachelor-thesis at the Secure Software Engineering Group about Android Security.
Title: Evaluating the Effectiveness of Android Malware Detection Approaches

We are looking for an interested student who wants to write her/his bachelor-thesis at the Secure Software Engineering Group about Android Security.
Title: Evaluating the Effectiveness of Android Malware Detection Approaches
To facilitate an early dissemination, we are today making available the following technical report. It outlines our vision of how static security code-analysis tools can be made more interactive, by allowing for just-in-time interactions. This is a collaboration with Ben Livshits from MSR.
Toward a Just-in-Time Static Analysis , Technical report TUD-CS-2015-1167, EC SPRIDE, 2015.
We are a group of researchers from TU Darmstadt, Germany, who work on creating tools to help developers use cryptography in their Java applications.
We are looking for developers who use Java cryptography APIs to answer a short 10-minute survey.
Our goal is to understand what cryptography tasks are usually performed, any difficulties developers face, and what would help Java developers use cryptography more correctly/efficiently.
Your participation is voluntary and completely anonymous. To participate, please fill in the survey at the following link http://tiny.cc/java_crypto_survey
Thanks!
Please feel free to forward this invitation to any Java developers you might know.
Sarah Nadi, Stefan Krüger, Mira Mezini, and Eric Bodden
I am happy to announce that for 2016 I have confirmed membership in the program committees in all of the major software engineering conferences, i.e., ICSE, FSE and ASE. ISSTA disallows invitations for the third time in a row, which is why I will contribute as co-chair of the artifact evaluation. Also I will be a member of the CODASPY PC. For ASPLOS, the reviewing period clashes with the one of ICSE, which is why I decided to only contribute to the ERC. Let there be many good submissions!
 A few weeks ago, the German edition of Technology Review interviewed me on the state of software security. The article is available now.
A few weeks ago, the German edition of Technology Review interviewed me on the state of software security. The article is available now.
Please consider submitting your research papers to ESSOS’16 which will take place in April at Royal Holloway London. We have been able to put together an excellent program committee. Submission deadline is October 2nd.
On our website we have now available two new papers accepted at ISC. The first paper originated out of our collaboration with SAP. It reports on a qualitative empirical study determining Factors Impacting the Effort Required to Fix Security Vulnerabilities. Thanks to our collaborators for the great work! The second work is on Dynamically Provisioning Isolation in Hierarchical Architectures, a novel, lightweight and effective means to counter side channels and covert channels in the cloud. Enjoy!
Steven will give a talk about CodeInspect at the leading international conference on software development GOTO Copenhagen. We are looking forward for a great conference.
Title of the talk: “All Your Code Belongs To Us – Dismantling Android Secrets With CodeInspect”
Abstract of the talk:
Several new papers written by members of the Secure Software Engineering Group have now been accepted at renowned international venues. The papers cover topics such as the reduction of false positives in static data flow analysis, the in-depth analysis of modern, sophisticated malware applications, and the challenges of developing secure software using agile techniques.
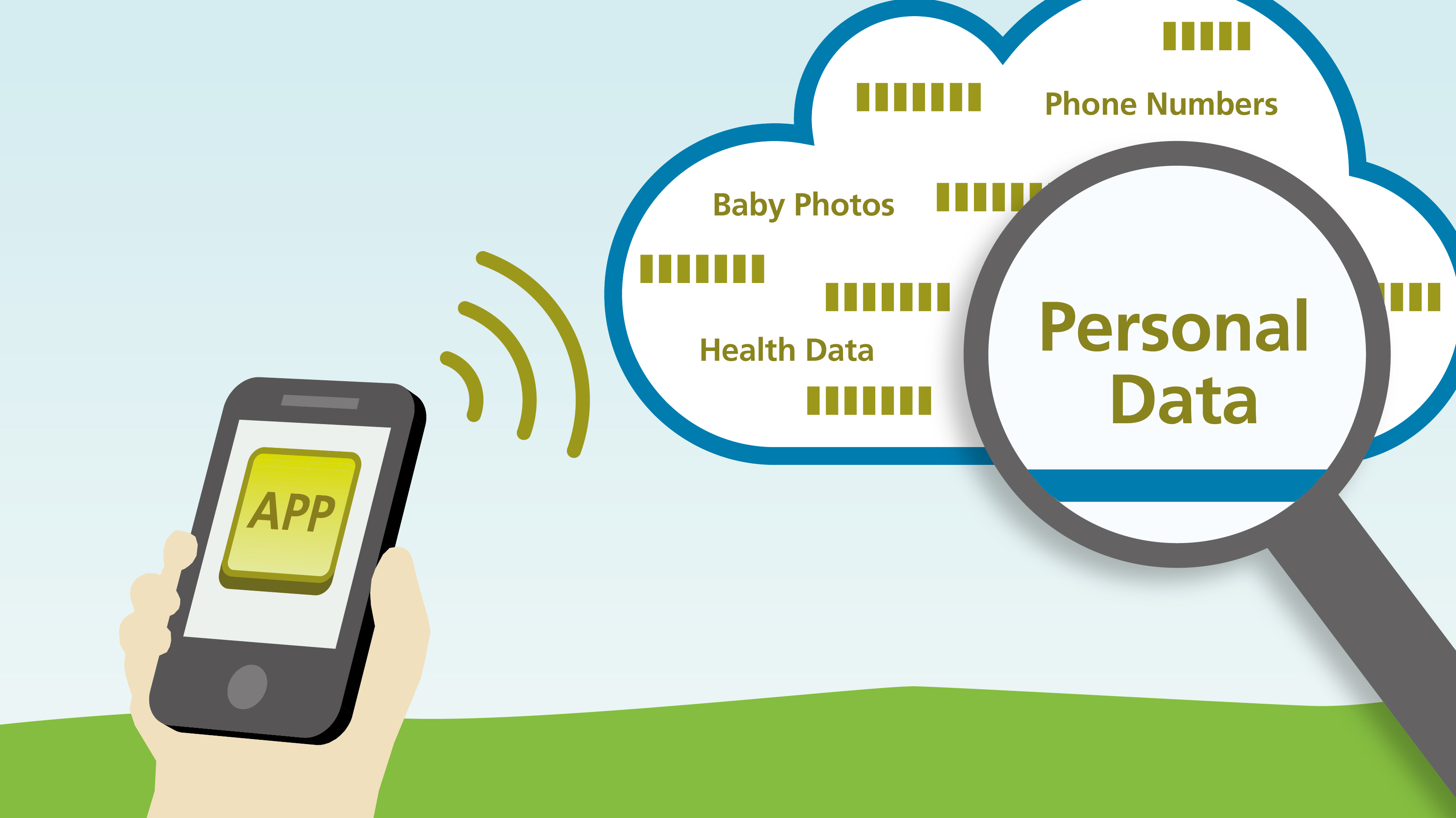
With the help of CodeInspect, Appicaptor and an internally developed tool, researchers from TU Darmstadt and Fraunhofer SIT have found that many mobile applications store private information in the cloud, in an easily accessible manner.
Many users of mobile applications want their data to be synced across multiple platforms (iOS/Android/Windows/OSX/…). For app developers it is typically hard to support synchronization, as they need to set up backend servers on which the data can be stored and synchronized. Cloud providers such as Amazon and Parse.com therefore provide backends as a service (BaaS). With BaaS, app developers can simply connect to pre-configured servers using a few lines of program code. This makes data storage and synchronization through the cloud very easy. Some apps use BaaS to share public data, which is ok as long as the data is configured to be read-only. Many apps, however, use BaaS also to store confidential data such as user names, email addresses, contact information, passwords and other secrets, photos and generally any kind of data one can think of. Such data should only be accessible to the individual app user who stored the data. The researchers found more than 56 million sets of unprotected data, including email addresses, passwords, health records and other sensitive information of app users, which may be easily stolen and often manipulated. Read the official release here.