As Golem and Heise are writing today, Google has updated its rules for advertisement in Android Apps. Earlier this year, researchers from the SSE group and from Fraunhofer SIT have found that almost one third of the top apps in Google’s Play store use advertising services that in many instances violate the store’s content policy. The result is annoying for users, as these apps will plague them with very intrusive forms of advertisement that can be very hard to eliminate even for expert users. Early on, we have shared these results with Google. The change by Google now obligates app developers to ensure that the ad frameworks they include in their app do not use any ad services violating Google’s policy.
Currently, the Google Play Store contains nearly 700000 apps . Most of them can be downloaded for free. These apps are developed by different kinds of developer, like hobby or semiprofessional developers or by actual software companies. To make some profit or get an allowance developers can augment these free apps with advertisement.
Advertising companies, such as leadbolt or airpush provide ready made ad libraries that developers can easily include in an application.
One can distinguish between “passive” and “active” forms of advertising. By a “passive” advertising, we mean simple banner advertisement which is included in the application’s GUI. It can be compared with web-banner advertising. In a special part of the application GUI, e.g., at the top or at the bottom of the application, small advertising banners are shown, while the app is running. We chose the category “passive” because the advertisement banner is only active if the application is running. When the user quits or closes the application the advertisement is not running any longer.
“Active” advertising plugins, on the other hand, are running independent of the application. After installing an application containing such a plugin and starting it, the included plugin installs a service onto the user’s phone which is running and will remain running in the background. This service has a connection to the advertisement network/provider who broadcasts to the device advertisement in the form of notifications or message boxes. This form of advertisement is called push advertising. Push advertisements can be perceived in different ways, such as
- advertisement notifications in the notification bar
- new apps installed on the launcher (basically a shortcut to some advertisement websites or links to apps on the Google Play store)
- popup messages
- …
Most of the time, the only possibility to remove this kind of advertisement is by deinstalling the application. Google itself defines policies for the handling of applications in its developer content policy rules. The most important for this article are the following:
[…]Products or the ads they contain also must not mimic functionality or warnings from the operating system or other applications.[…]
[…]It must be clear to the user which app each ad is associated with or implemented in. Ads must not make changes to the functioning of the user’s device outside the ad by doing things such as installing shortcuts, bookmarks or icons or changing default settings without the user’s knowledge and consent. If an ad makes such changes it must be clear to the user which app has made the change and the user must be able to reverse the change easily, by either adjusting the settings on the device, advertising preferences in the app, or uninstalling the app altogether. Ads must not simulate or impersonate system notifications or warnings.[…]
We analysed different kinds of push advertisement providers and found that most of them do violate the mentioned policies above. In the following we want to show how aggressive the push advertisement is and that most of the time the user is not able to identify which application caused the advertisement:
Unidentifiable Adds in the notification bar:
The left picture (with the green check mark) shows an advertisement conforming with Google’s content policy. The application (“Lie Detector”), which causes the advertisement is shown small, but still identifiable, together with the advertisement’s company URL “xapush.com”. In contrast, the right picture shows an example that violates Google’s content policy, because a mobile device user is not able to identify the source application of that advertisement. This means that to disable those ads the user has to deinstall apps one by one until finally uninstalling the app which causes the push advertisement. This is especially problematic since ad libraries show the notifications only from time to time. Therefore even after installing an app one cannot be sure if it was the right one (the one causing the ad) until an amount of time has elapsed that is large enough to be sure that probably no ads will be shown any longer. This is anything but user friendly but ad frameworks like this are included in real-world applications.
Security messages in form of Android’s pop-up messages:
 This screenshot shows an Android message box which pops up at some time (the application with the advertisement does not even have to be open!). It is just an example of the different messages that pop up, but it shows a message in German “Schützen Sie Ihr Telefon!” which means “Protect Your Mobile Device!”. If the user clicks on “Download”, she gets forwarded to a website which sells anti-virus software. For a mobile device user without any security knowledge it is hard to know that this message does not come from Android itself as some kind of internal anti-virus detection mechanism. Instead, it is just an advertisement. These kinds of messages do violate Google’s content policy and -much worse- fool the user with security-related information.
This screenshot shows an Android message box which pops up at some time (the application with the advertisement does not even have to be open!). It is just an example of the different messages that pop up, but it shows a message in German “Schützen Sie Ihr Telefon!” which means “Protect Your Mobile Device!”. If the user clicks on “Download”, she gets forwarded to a website which sells anti-virus software. For a mobile device user without any security knowledge it is hard to know that this message does not come from Android itself as some kind of internal anti-virus detection mechanism. Instead, it is just an advertisement. These kinds of messages do violate Google’s content policy and -much worse- fool the user with security-related information.
Illegal shortcuts on the launcher:
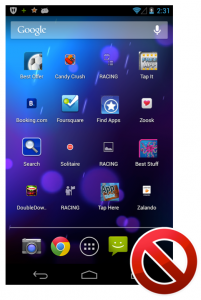
The screenshot above shows the device launcher after a day with only one installed application with push advertisement in it. After one day, there were 21 shortcuts installed on the launcher. The shortcuts are mostly links to either an advertisement website or a special application in Google Play (e.g., Solitär). As the picture shows, the user is not able to identify which application installed those shortcuts. This causes the same situation as described in point one, the user has to deinstall app by app until she reaches the app that causes the creation of those shortcuts.
We analysed around 10 000 apps from the Google Play Store (including apps from different categories such as “games”) to find push advertisement. We used parts of the URANOS framework , and found that 25% of those apps include push advertisements that could cause the violations as described above.
We informed Google about our findings and they confirmed that these kind of “features” of the push advertisement (as described above) do violate their content policy. Furthermore, we also suggested that Google should update their content policy and suddenly the policy got updated and describes in more details the do’s and dont’s (we can only guess that the update belonged to our report to Google!). Some parts of the updated version of the content policy can be seen above.
Unfortunately, the situation of the 25% of apps including policy-violating features did not change. A few weeks ago we did a second test with the top 1000 apps from the Google Play store (again including apps from different categories such as “games”) and the number of push advertisements has even increased up to 30%.
What can be done against this policy violation?
Google’s typical response to apps that violate its content policy is to remove those apps from the app store. But in this case not the apps themselves nor their developers are actually to blame. Many developers include ad libraries blindly, simply trusting that they will conform to such policies. The removal of single apps also does not solve the problem as all other apps including the same push-ad library will still cause the same problems. We thus believe that app-store owners like Google should work together with ad-library developers to negotiate that future versions of ad libraries at least support a mode that can be chosen such that libraries conform to content policies.
Update:
An additional update of the Google Content Policy happened a few days ago where Google makes it more explicit and wrote each app developer an email which says that they have 30 days to inspect their apps about the compliance violations mentioned above.
Stephan Huber and Siegfried Rasthofer


